Platform with Auth Keycloak
Keycloak is an Identity Access Management (IAM) and Single-sign-On tool that can be used to facilitate authentication and authorization processes on an application. With the Single Sign On system, user authentication is centralized at one point so that all devices have the same credentials even having the same web session, once logged in then no need to log in again.
Some features on Keycloak are :
- Protocol standard SAML OpenID Connect, dan Oauth2
- LDAP Integration
- Social Login (Facebook, Twitter, Gmail, dll)
- Identity Brokering
- Single-Sign On
- Admin management
- Admin API
- Access Control
Flow Keycloak in Qoin Service
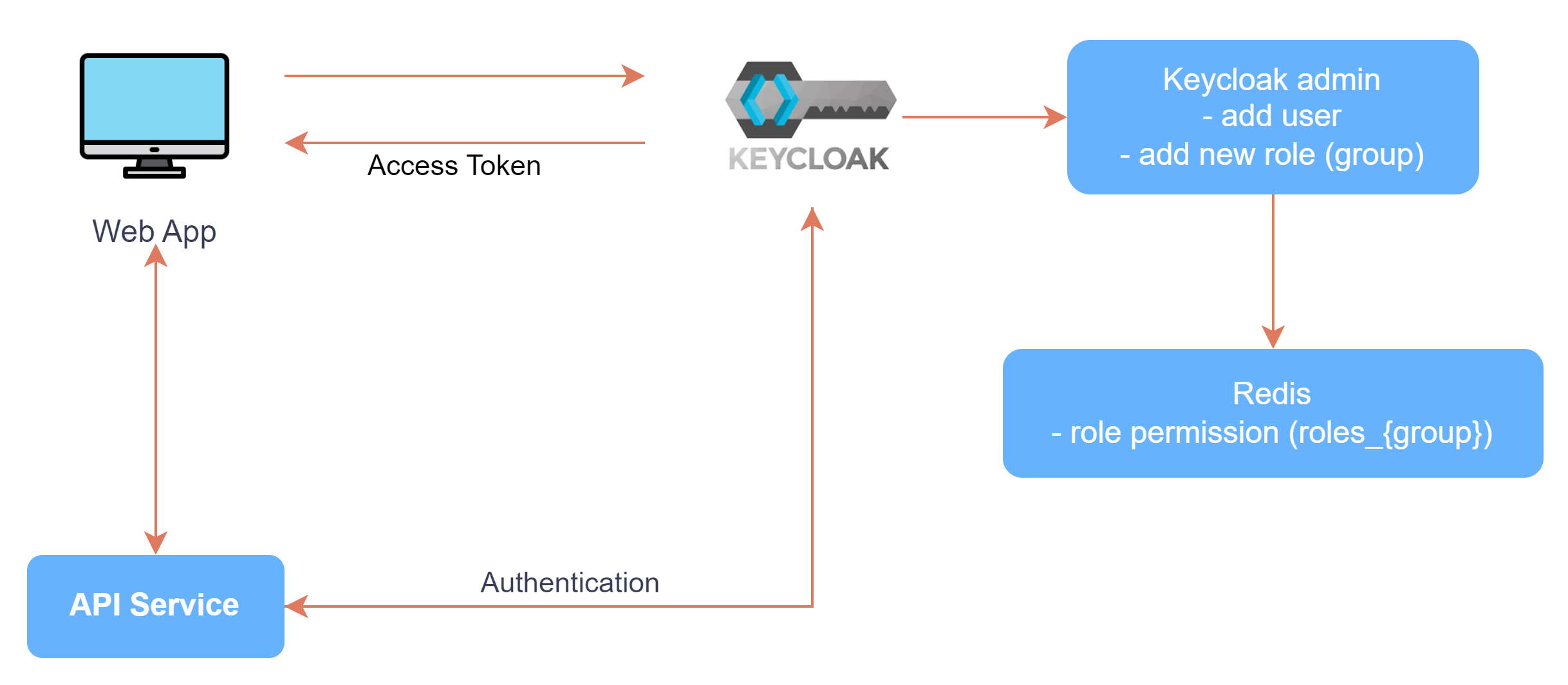
The web admin of the Qoin Service will be registered through Keycloak by the super admin who manages the KeyCloak.
Data required for client integration to Keycloak :
| Name | Description |
|---|---|
| ClientId | Client Name/Id. |
| ClientSecret | Generate from Client Credentials |
| Realm | A realm is a space to manage objects, including users, applications, roles, and groups. |
| Host | Server hostname. |
Flow Process to Create Role and Role Permission
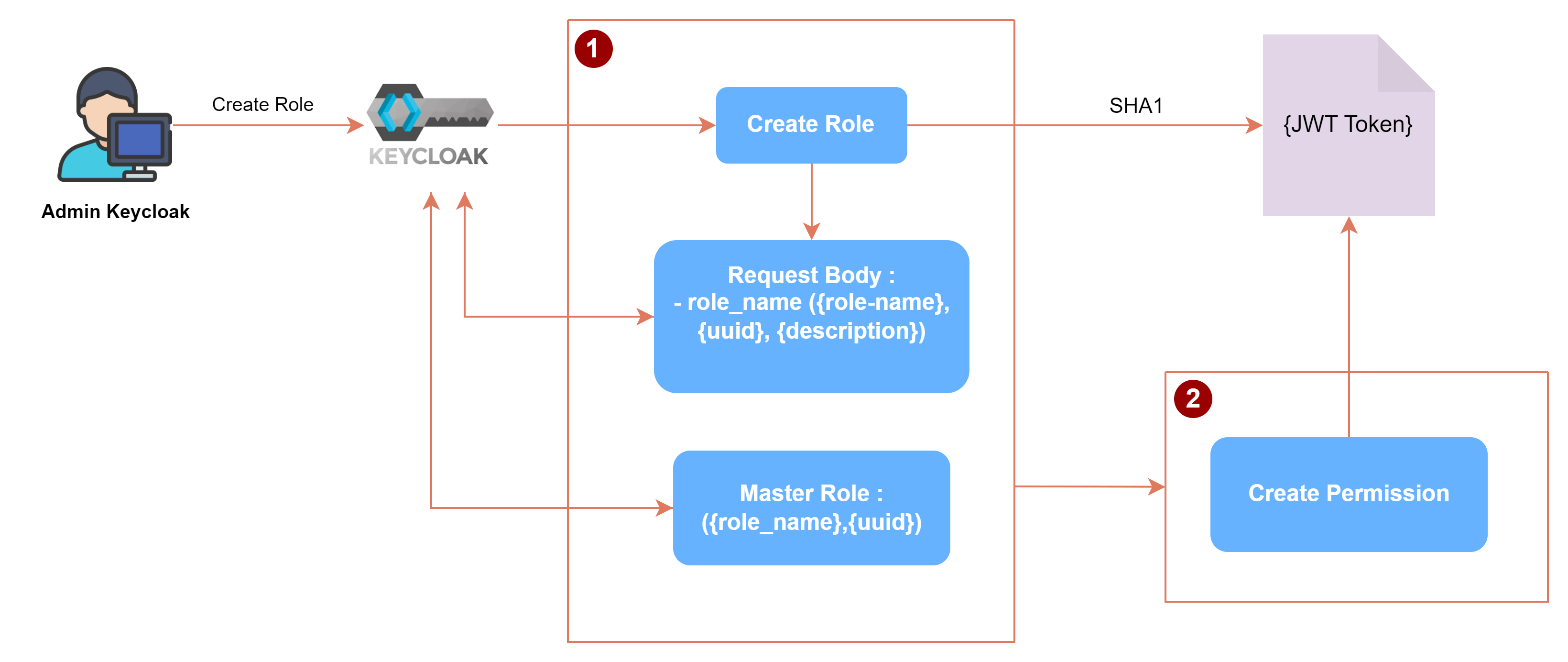
Story of flow :
- The Keycloak admin will create a new role on the Keycloak. Previously, the admin must be able to access the Realm according to the project to be accessed.
- Data for the Request body is {rolename} that already contains data {rule_name }{uuid}_{description}.
- The Master Role data will be obtained from ({role_name},{uuid}) which will be synchronized with the role.
- The data will then be encrypted using SHA1 and the result is a JWT Token.
Updated 9 months ago
